For several time now, iOS and Android have supported MAC randomization, which is a way to change dynamically the MAC address used to communicate with a WiFi network.
A device must identify itself to the network using a unique network address called a Media Access Control (MAC) to communicate with a WiFi network.
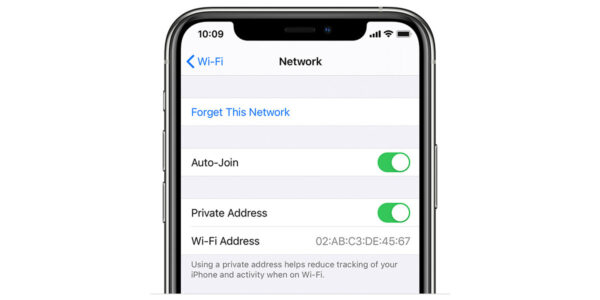
The intent of device manufacturers like Apple, Samsung… is to prevent the device’s activity and movement from being tracked on networks.
The MAC Randomization or Private Address option is on by default in iOS 14, iPad 14, and watchOS 7.
Even though the final iOS 14 release has less aggressive randomisation behaviour than betas, the world of MAC randomization is changing.
From a user’s point of view, this might be a good thing as anonymity is back. But is that always welcome?
If you think back to the last time you stayed at a hotel enjoying free WiFi, you had to enter your username only once. The day after, while drinking your coffee at the swimming pool, you could surf without entering your username.


The network knew you’d already logged in as they matched the login with the device’s MAC address.
Now, if the MAC address is randomized, the different places (with different SSID) inside the same hotel cannot know that the device is the same, as the MAC is new. Users are forced to sign in again and again.
By this point, you are asking how to solve it
Actually, there is a solution to mitigate the impact of MAC address randomization and solve your headaches.
Use for every Access Point under the Hotspot Gateway, the same SSID, to make the mobile devices not randomize their MAC address for each AP.
Make sure that the Keep-Alive Timeout, DHCP Lease, Session Timeout have been adequately set to grant a total time for the users’ journey, without the need to re-login every X time.
